Question: 1
The exhibit shows a router with three interfaces E0, E1 and S0. Interfaces E0 and E1 are connected to internal networks 192.168.10.0 and 192.168.20.0 respectively and interface S0 is connected to the Internet. The objective is to allow two hosts, 192.168.20.16 and 192.168.10.7 access to the Internet while all other hosts are to be denied Internet access. All hosts on network 192.168.10.0 and 192.168.20.0 must be allowed to access resources on both internal networks. From the following, select all the access list statements that are required to make this possible.
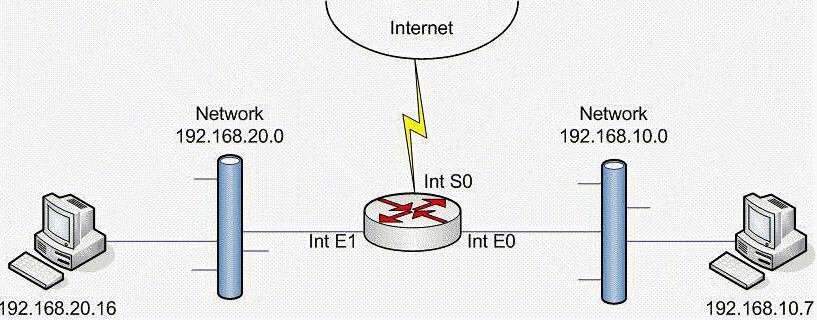
Question: 2
After installing Snort on your Windows machine that is destined to be your IDS, you need to edit the configuration file to customize it to your needs. What is the name of that configuration file?
Question: 3
You are a host in a network segment that has IP addresses in the range of 10.0.16.1~10.0.31.254. You need to create an access control list that will filter your segment of addresses. Which of the following is the wildcard mask that will be used to filter your network segment?
Question: 4
You are going to configure your SuSe Linux computer to run Snort as your IDS. Prior to running Snort, you wish to configure Apache and PHP, so you may use Snort monitoring tools in the browser. You need to verify that Apache and PHP are running properly. What line needs to be entered in the info.php file to test PHP on your Apache server?
Question: 5
As Intrusion Detection Systems become more sophisticated, the software manufacturers develop different methods of detection. If an IDS uses the process of matching known attacks against data collected in your network, what is this known as?