Question: 1
Exhibit:
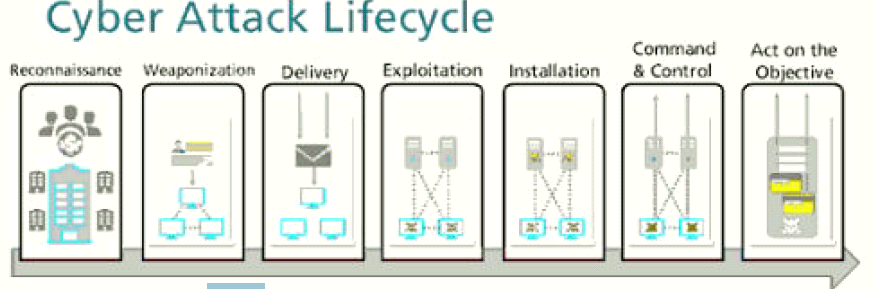
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?
Question: 2
Exhibit:
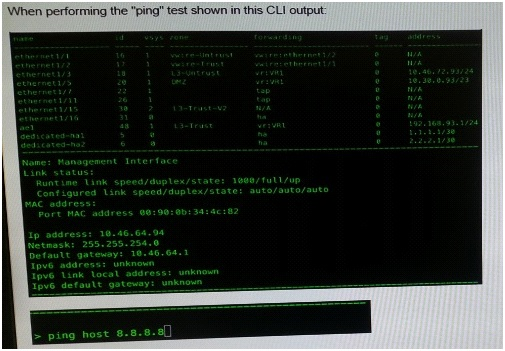
What will be the source address in the ICMP packet?
Question: 3
An internal system is not functioning The firewall administrator has determined that the incorrect egress interface is being used After looking at the configuration, the administrator believes that the firewall is not using a static route
What are two reasons why the firewall might not use a static route'? (Choose two.)
Question: 4
Which two methods can be used to verify firewall connectivity to AutoFocus? (Choose two.)
Question: 5
What happens when en A P firewall cluster synchronies IPsec tunnel secunty associations (SAs)?