Question: 1
An organization has implemented a control for penetration testing and red team exercises conducted on their network. They have compiled metrics showing the success of the penetration testing (Penetration Tests), as well as the number of actual adversary attacks they have sustained (External Attacks). Assess the metrics below and determine the appropriate interpretation with respect to this control.
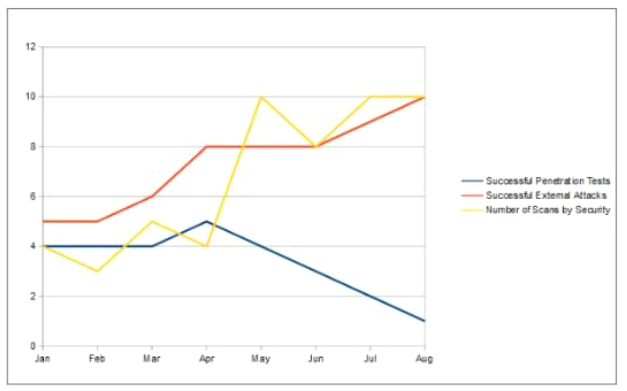
Question: 2
Which of the following can be enabled on a Linux based system in order to make it more difficult for an attacker to execute malicious code after launching a buffer overflow attack?
Question: 3
A security incident investigation identified the following modified version of a legitimate system file on a compromised client:
C:\Windows\System32\winxml.dll Addition Jan. 16, 2014 4:53:11 PM
The infection vector was determined to be a vulnerable browser plug-in installed by the user. Which of the organization's CIS Controls failed?
Question: 4
Allied services have recently purchased NAC devices to detect and prevent non-company owned devices from attaching to their internal wired and wireless network. Corporate devices will be automatically added to the approved device list by querying Active Directory for domain devices. Non-approved devices will be placed on a protected VLAN with no network access. The NAC also offers a web portal that can be integrated with Active Directory to allow for employee device registration which will not be utilized in this deployment. Which of the following recommendations would make NAC installation more secure?
Question: 5
Which of the following assigns a number indicating the severity of a discovered software vulnerability?