Question: 1
SIMULATION
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday.
The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations.
The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
INSTRUCTIONS
Review the network architecture and supporting documents and fulfill these requirements:
Part 1:
Analyze the configuration of the following components: DNS, Firewall 1, Firewall 2, Router 1, Router 2, VPN and Orchestrator Server.
Identify the problematic device(s).
Part 2:
Identify the correct options to provide adequate configuration for hybrid cloud architecture.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part 1:
Cloud Hybrid Network Diagram
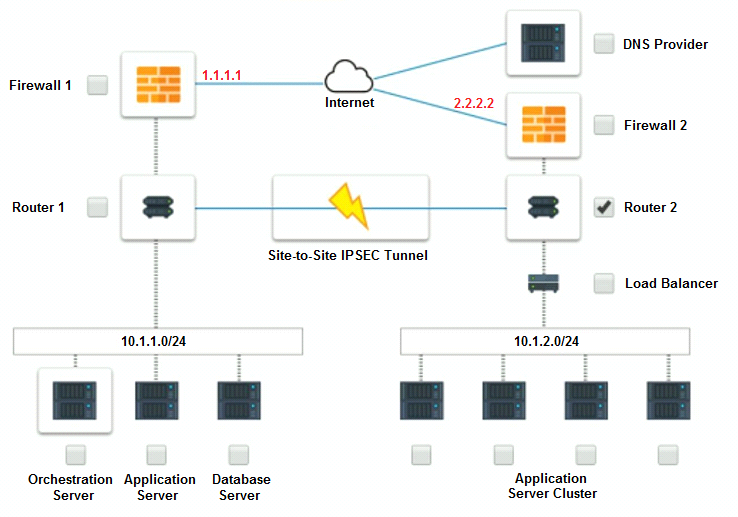
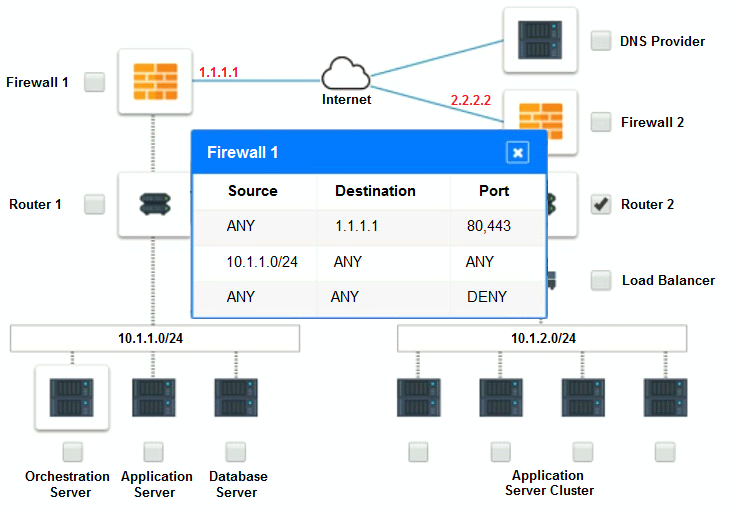
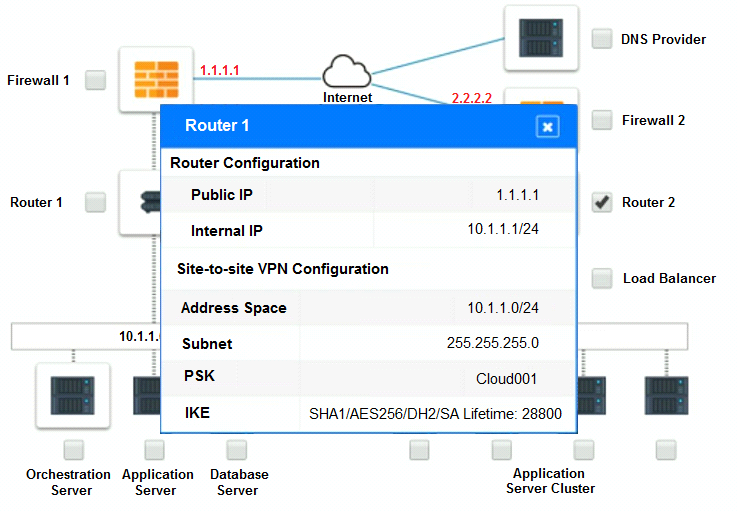
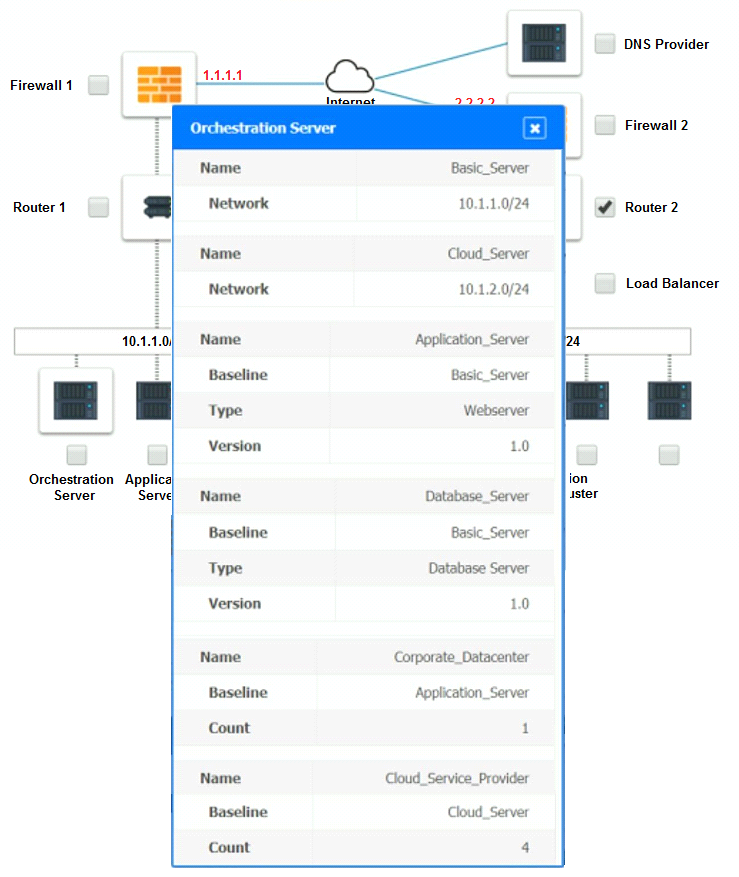
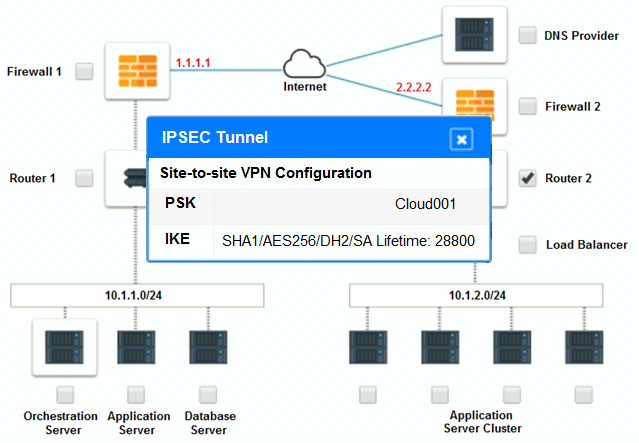
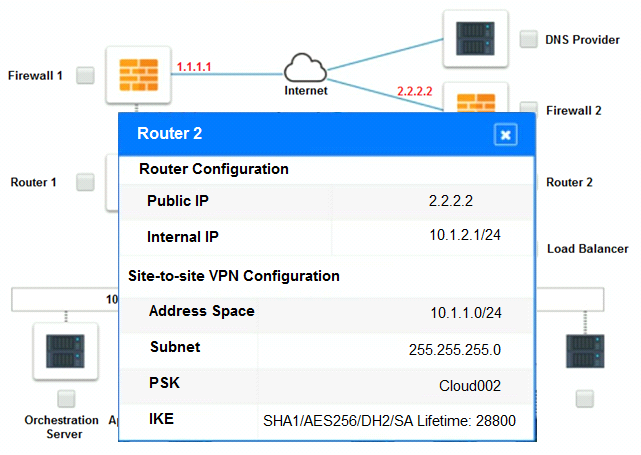
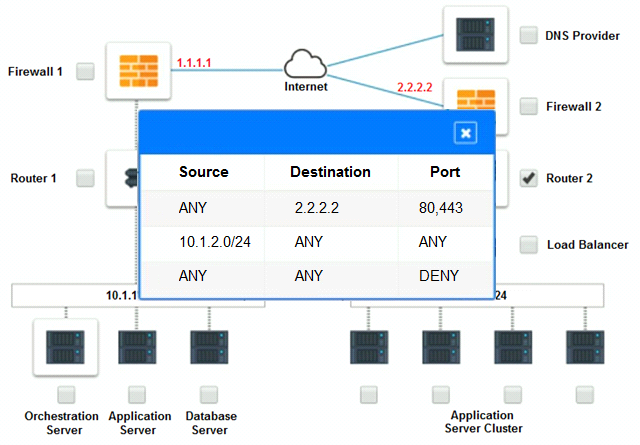
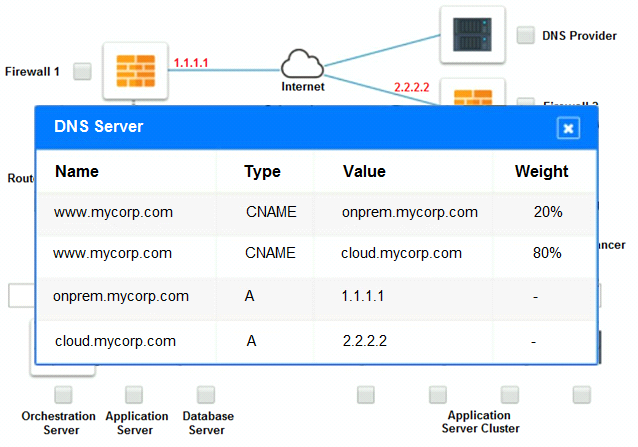
Part 2:
Only select a maximum of TWO options from the multiple choice question
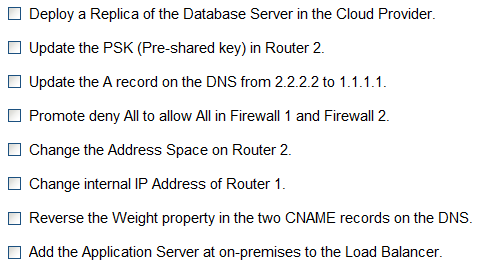
Question: 2
SIMULATION
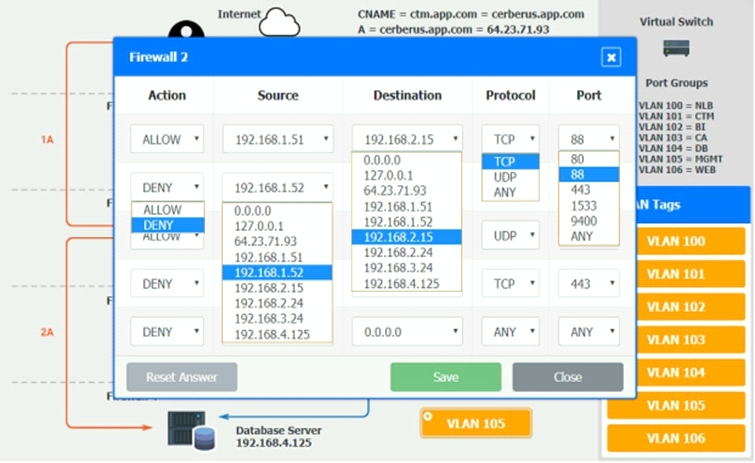
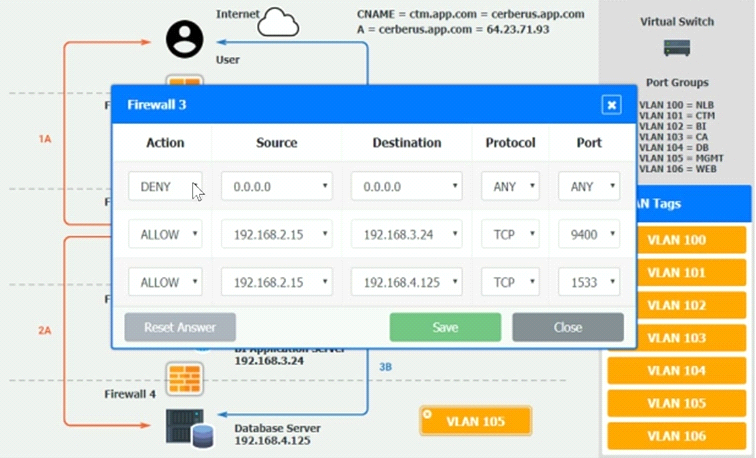
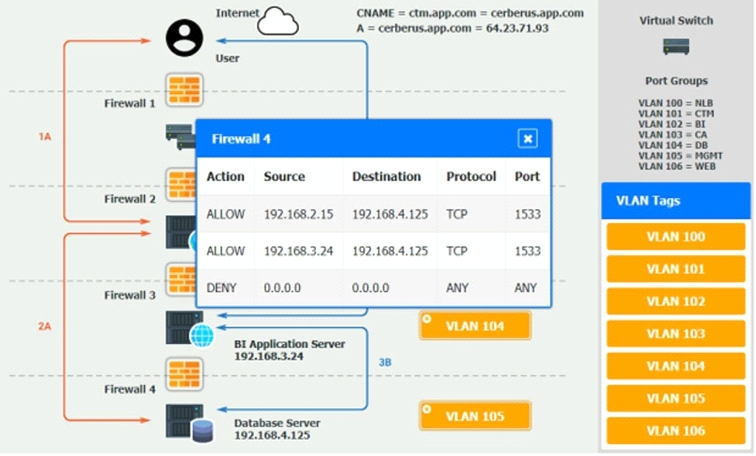
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
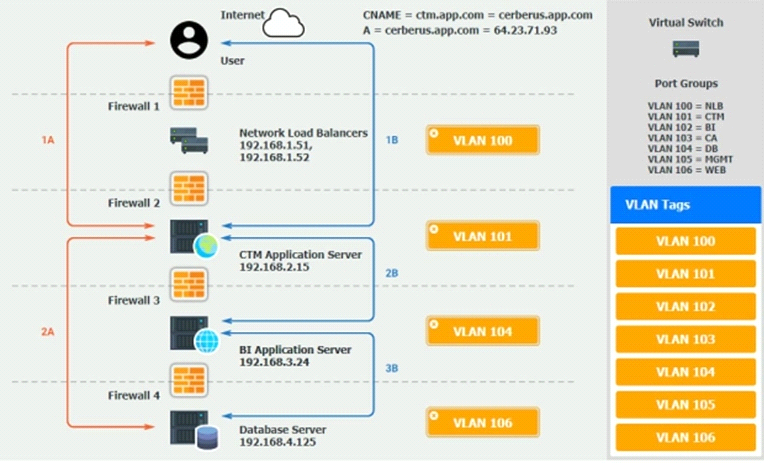
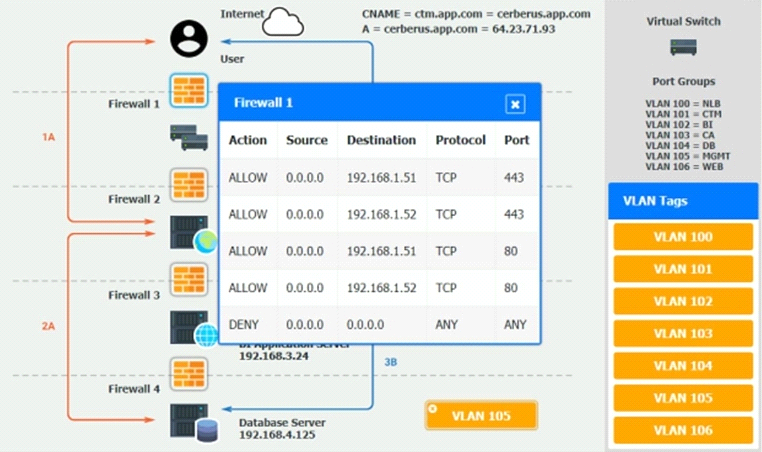
1A -- The end user accesses the application through a web browser to enter and view clinical data.
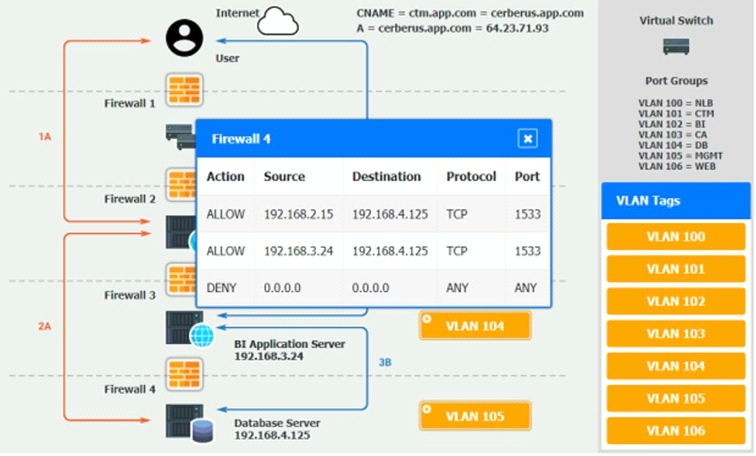
2A -- The CTM application server reads/writes data to/from the database server.
1B -- The end user accesses the application through a web browser to run reports on clinical data.
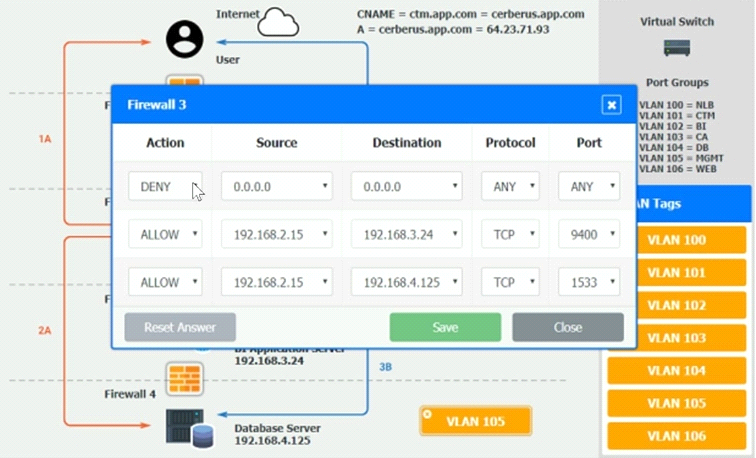
2B -- The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B -- The BI application server gets the data from the database server and presents it to the CTM application server.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
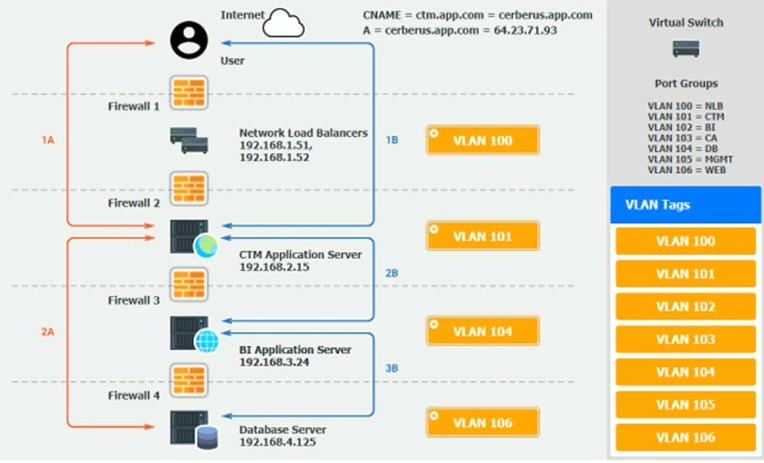
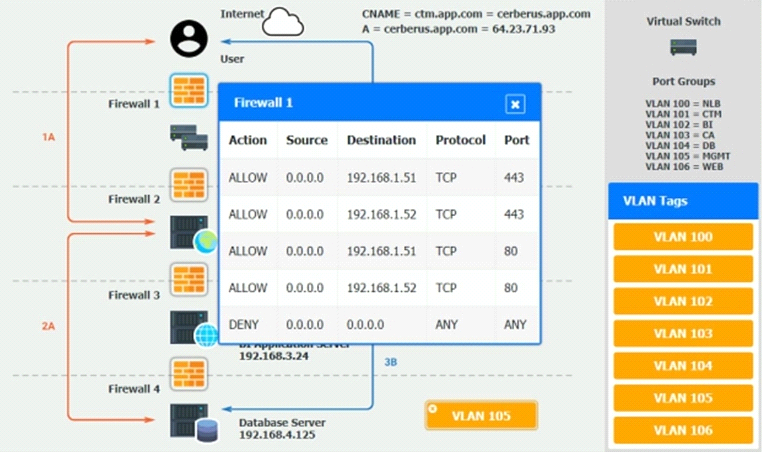
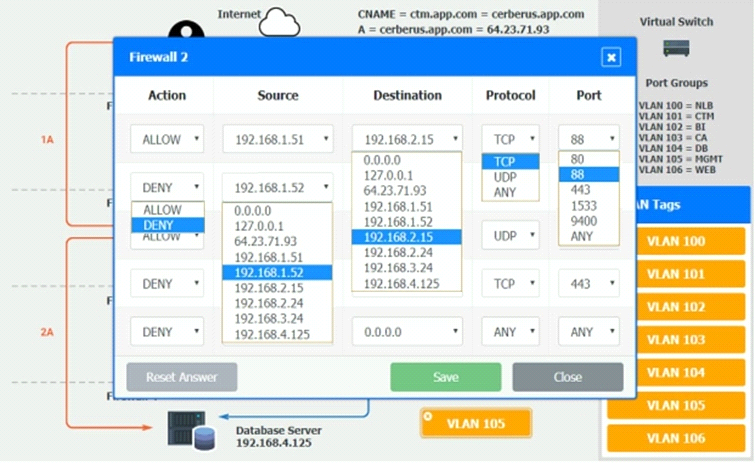
Question: 3
After accidentally uploading a password for an IAM user in plain text, which of the following should a cloud administrator do FIRST?
Question: 4
A systems administrator is troubleshooting performance issues with a Windows VDI environment. Users have reported that VDI performance is very slow at the start of the work day, but the performance is fine during the rest of the day.
Which of the following is the MOST likely cause of the issue?
Question: 5
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A -- The end user accesses the application through a web browser to enter and view clinical data.
2A -- The CTM application server reads/writes data to/from the database server.
1B -- The end user accesses the application through a web browser to run reports on clinical data.
2B -- The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B -- The BI application server gets the data from the database server and presents it to the CTM application server.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Answer : A
Show Answer
Hide Answer