Question: 1
What are two recommendations for protecting network ports from being exploited when located in an office space outside of an IT closet? (Choose two.)
Question: 2
Refer to the exhibit. Router R2 is configured with multiple routes to reach network 10.1.1.0/24 from router R1. Which path is chosen by router R2 to reach the destination network 10.1.1.0/24?
Question: 3
Refer to the exhibit. The entire MAC address table for SW1 is shown here:
SW1#show mac-address-table
Mac Address Table
Vlan Mac Address Type Ports
000c.8590.bb7d DYNAMIC Fa0/1
010a.7a17.45bc DYNAMIC FaO/3
7aa7.4037.8935 DYNAMIC FaO/4
SW1#
What does SW1 do when Br-4 sends a frame to Br-2?
Question: 4
Refer to the exhibit. Router R4 is dynamically learning the path to the server. If R4 is connected to R1 via OSPF Area 20, to R2 via BGP, and to R3 via EIGRP 777, which path is installed in the routing table of R4?
Question: 5
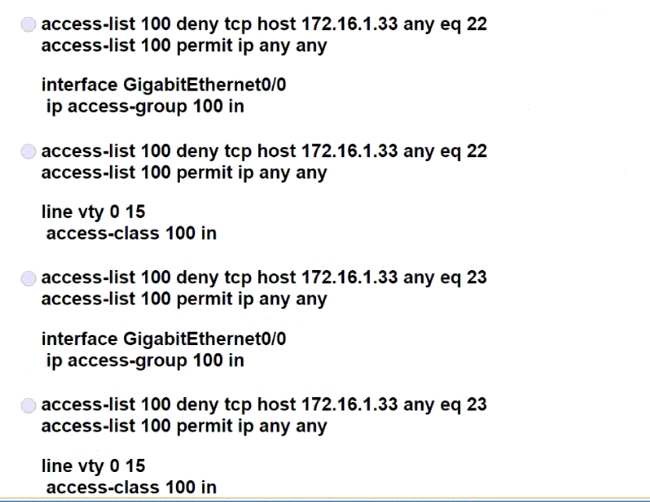
Refer to the exhibit. Which configuration for RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?